To professional analysts, it has long been clear that the “Russiagate” saga – including the “Russian hacking” claims, the Trump-Russia collusion claims, as well as the “Skripal poisoning incident” and the more recent “Navalny poisoning incident” – has been a US and NATO psychological operation aimed at containing a resurgent Russia and a somewhat unpredictable US President.
Several aspects of the “Russian hacking” psychological operation had already been uncovered by independent researchers like Stephen McIntyre, “Adam Carter” and “The Forensicator”. In early November, however, British researcher David J. Blake essentially solved the “Russian hacking” psyop, down to the operational level, as described in his new book “Loaded for Guccifer 2.0”.
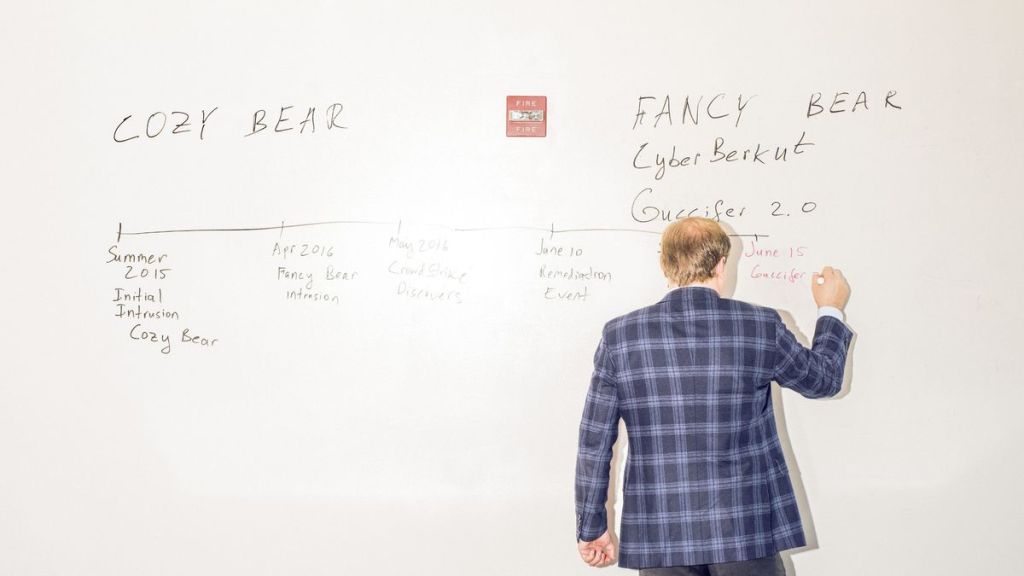
Blake shows how the “Russian hacking” psyop was initiated by the US and NATO in 2014 in response to Russia’s reaction to the US regime change in Ukraine, when Russia retook control of the Crimean Peninsula and supported the de-facto secession of Russian-speaking eastern Ukraine.
The US/NATO psyop was inspired by the actual amateur hackers “CyberBerkut” in Ukraine and “Guccifer” in Romania. Blake shows how in 2014, NATO created a “Cyber Defence Trust Fund” and used this entity to initiate false-flag “hacking operations” against the US and other NATO members that would then be falsely “attributed” to alleged Russian “state-sponsored hacking groups”.
Regarding the most prominent such case, the alleged “hacking” of the US Democratic Party (DNC) and the 2016 Hillary Clinton presidential campaign, Blake shows how the emails and documents in question were in fact exfiltrated by the FBI and FBI cybersecurity contractor CrowdStrike, whose founder, Dmitri Alperovitch, is a Senior Fellow at the US-NATO think tank Atlantic Council. (1)
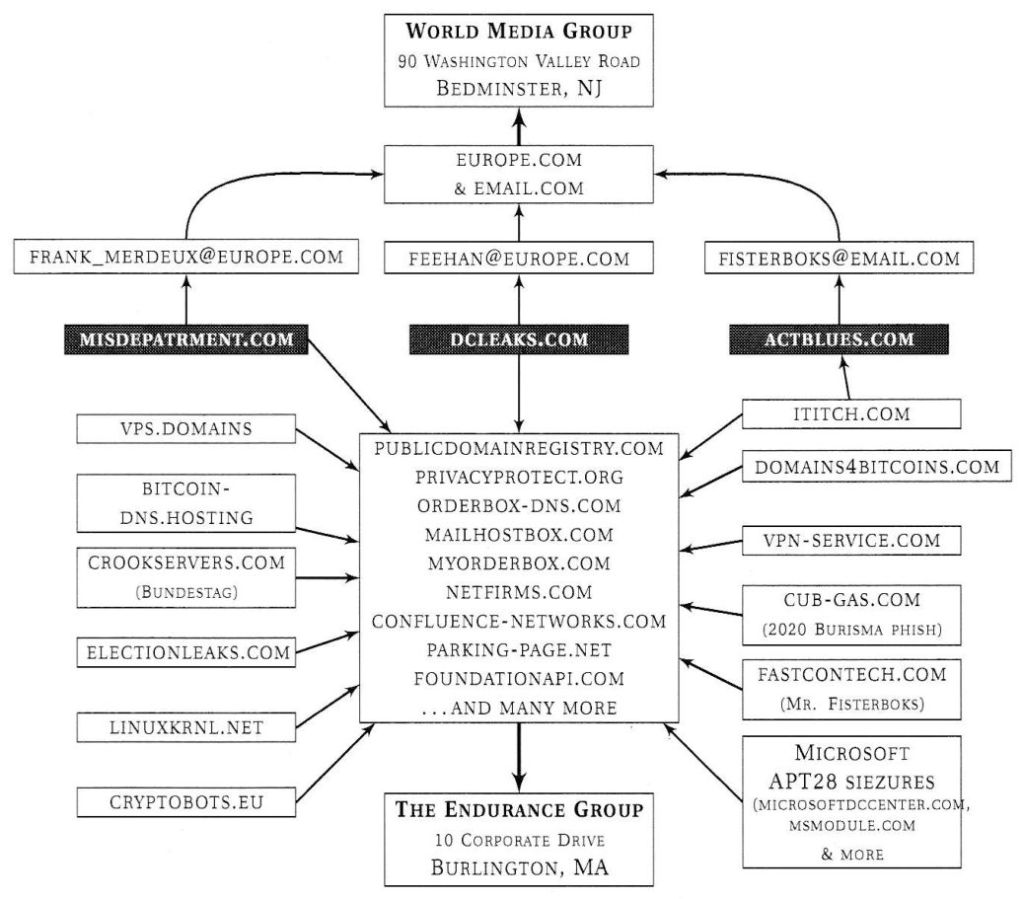
Blake shows how the mysterious persona of Guccifer 2.0, who claimed the hack, was played by none other than Alperovitch himself, while the technical infrastructure, including the notorious website dcleaks.com, was provided by US and NATO intermediaries in NATO member Romania.
Later, former FBI director Robert Mueller would pretend to “investigate” the cyber operation, attributing it to alleged “Russian hacking groups” named “Cozy Bear” and “Fancy Bear” based on information provided by FBI and DNC contractor CrowdStrike and its CTO Dmitri Alperovitch. (2)
Blake also shows how other alleged “Russian hacks”, including the “hacking” of the German parliament in 2015, relied on the very same NATO-controlled technical infrastructure. Blake was able to show this based on archived information about previous owners of IP addresses, name servers, and SSL security certificates – all pointing to the US military, NATO, and the Ukrainian government. (3)

In the case of the staged hack of the US Democratic Party, Blake shows how FBI cybersecurity contractor CrowdStrike added false “Russian fingerprints” by embedding the documents into previously published CyberBerkut documents and inserting additional false signatures. However, CrowdStrike made a few technical mistakes that ultimately revealed their US time zone.
Blake highlights the important fact that in all of these false-flag “Russian hacks”, originating from NATO-controlled infrastructure, either no data or only trivial data was released to the public. Some questions continue to remain open, however, such as the role of murdered DNC employee Seth Rich and the actual source of Wikileaks, whose founder Julian Assange is still in British custody.
In the wake of the 2014 US regime change in Ukraine, the family of then Vice President Joe Biden exfiltrated millions of dollars from Ukraine, protected against corruption investigations by Joe Biden himself, as leaked phone recordings confirmed. As of 2021, the professionals behind the Ukraine regime change and the “Russiagate” pysop will once again be in full control of the US government.
Most US and European media have promoted the “Russiagate” and “Russian hacking” psyops and will continue to do so. This is because most US and European media, both liberal and conservative, are themselves embedded in networks linked to NATO and the US Council on Foreign Relations. It is only some independent media that have been seriously investigating these topics.
Are there real Russian state-sponsored hacks against Western targets? Yes. Blake argues that, for instance, the hacking operation against the British Institute for Statecraft and its “Integrity Initiative” – itself deeply involved in the “Russiagate” psyop – was likely a professional Russian operation. The problem is that such real operations are much harder to “attribute” than fake ones.
∗∗∗
Book: Loaded for Guccifer2.0: Following A Trail of Digital Geopolitics (2020) by David J. Blake
∗∗∗
(1) Another well-known Senior Fellow at the Atlantic Council is Eliot Higgins, founder of the Bellingcat group, which appears to serve as a civilian front organization of British military intelligence and was involved in psychological operations both in Ukraine and the Syria war.
(2) Blake was even able to show, based on archived IP address and SSL certificate data, that the FBI prepared its “Russia Special” operation on an “off-the-books”, inofficial web-based email system that was created by or for Robert Mueller during his time as FBI director (2001-2013).
(3) The alleged “Russian hacking” of the Swiss Ministry of Defense and Swiss arms manufacturer RUAG, in January 2016, may also have been a NATO false-flag operation.