On March 7th, 2017, Wikileaks released a giant file of 8,761 documents from the U.S. Central Intelligence Agency (CIA) codenamed Vault 7. Wikileaks called the leak the “first full part of the series “Year Zero”. The documents were stolen from a network that supposedly was “isolated” within the CIA itself.
The files include details on CIA’s software capabilities, such as the ability to compromise cars, smart TVs, web browsers and the operating systems of most smartphones, as well as other operating systems such as Microsoft Windows, macOS, and Linux. A CIA internal audit identified 91 malware tools out of more than 500 tools in use in 2016 being compromised by the release.
The leaks outlined how the CIA could pretty much hack into any device with a suite of tools designed to read and copy data from electronic devices. The documents detailed how, for example, authorities found a way to bypass encryption in a host of secure messaging apps such as WhatsApp and Telegram.
The CIA’s covert hacking division, had found a way to bypass vastly popular end-to-end encryption apps used on phones to prevent hacking and spying. This was accomplished by hacking the smartphone first. The code would run in the background and collect audio and text message traffic before encryption was applied through the apps.
What this means is that apps like WhatsApp, Signal, and Telegram — hugely popular because of their security features — were vulnerable. People using these apps could still be spied on by the CIA.
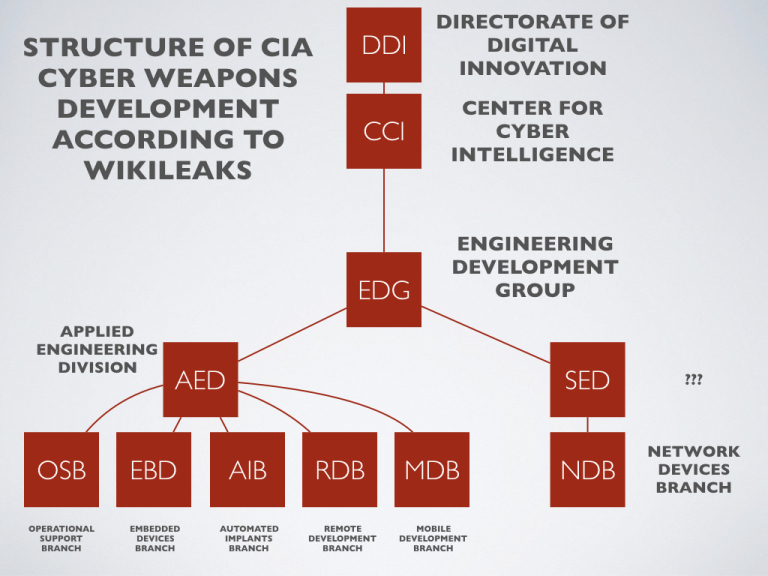
By the end of 2016, the CIA’s hacking division, which formally falls under the agency’s Center for Cyber Intelligence (CCI), had over 5,000 registered users and had produced more than a thousand hacking systems, trojans, viruses, and other ‘weaponized’ malware.
These techniques permit the CIA to bypass the encryption of WhatsApp, Signal, Telegram, Wiebo, Confide and Cloackman by hacking the “smart” phones that they run on and collecting audio and message traffic before encryption is applied.
According to WikiLeaks, once an Android smartphone is penetrated CIA can collect “audio and message traffic before encryption is applied”. Some of CIA’s software is reportedly able to gain access to messages sent by instant messaging services.
This method of accessing messages differs from obtaining access by decrypting an already encrypted message. While the encryption of messengers that offer end-to-end encryption, such as Telegram, WhatsApp and Signal, wasn’t reported to be cracked, their encryption can be bypassed by capturing input before their encryption is applied, by methods such as keylogging and recording the touch input from the user.
Send in your tips and submissions by filling out this form or write to us directly at the email provided. Join us on WhatsApp for more intel and updates.
GreatGameIndia is a journal on Geopolitics and International Relations. Get to know the Geopolitical threats India is facing in our exclusive book India in Cognitive Dissonance.







